Let’s say, hypothetically, you want to see the replay of Teddy Riner kicking ass at the Olympics.
But you’re not in France, so France TV blocks you if your IP is not French.
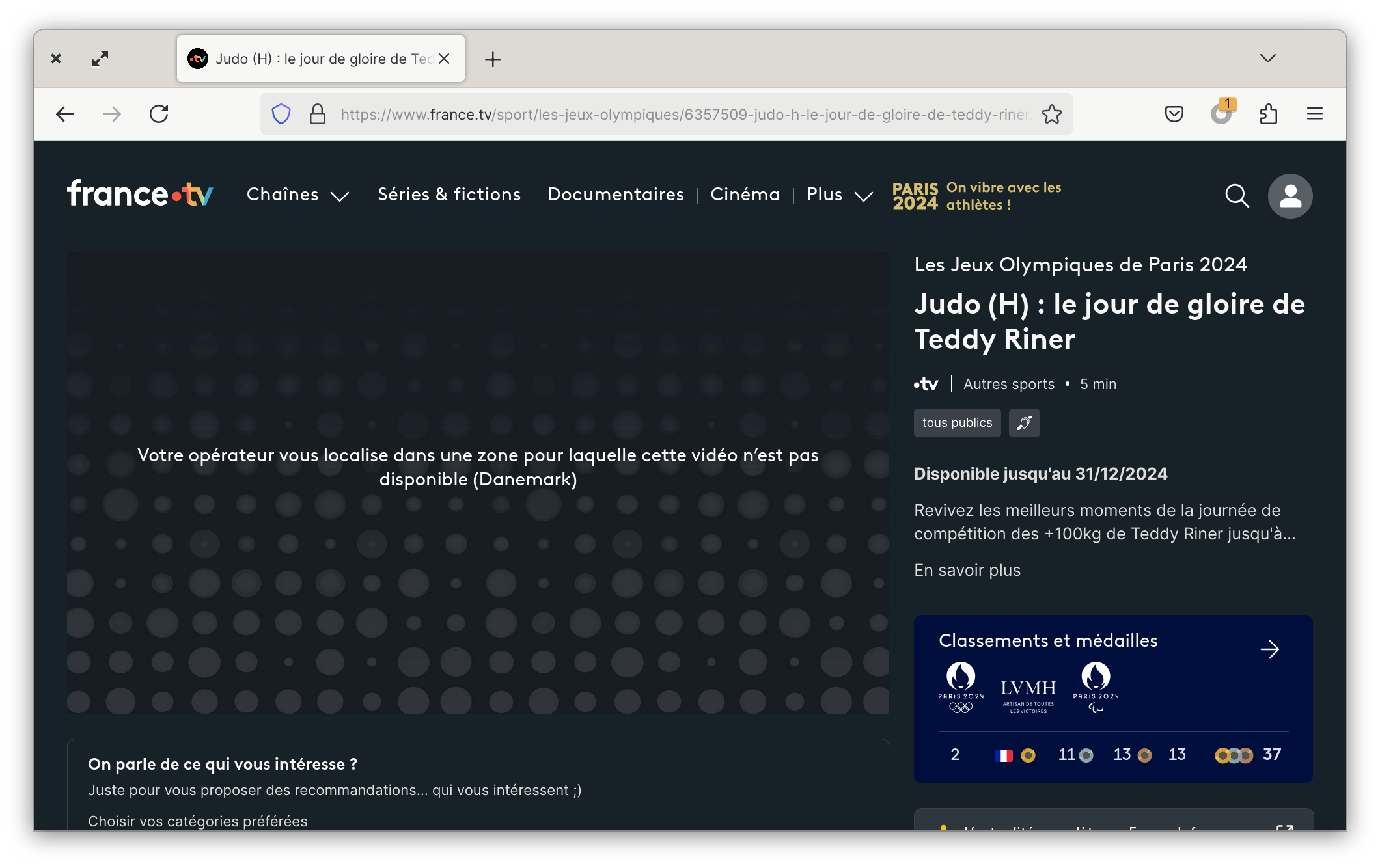
Your operator locates you in an area where this video is not available (Denmark).
At this point, you might think about taking a VPN subscription or find a free shaddy VPN that will inject malware into unencrypted HTTP pages.
SSH port forwarding to the rescue
Luckily I was already renting a Linux server (well, I forgot to cancel it), located in France.

You can use the following ssh command to create a SOCKS proxy.
ssh -fND 127.0.0.1:3000 username@server
With netstat, we can see that ssh is listening on port 3000.
$ sudo netstat -ltupn
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address
tcp 0 0 127.0.0.1:3000 0.0.0.0:* LISTEN 27833/ssh
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN 920/systemd-resolve
udp 0 0 127.0.0.53:53 0.0.0.0:* 920/systemd-resolve
We can now use the port 3000 as a proxy.
Personally, I use Switchy Omega to easily change between proxies. But you can modify directly the proxy settings of your web browser.
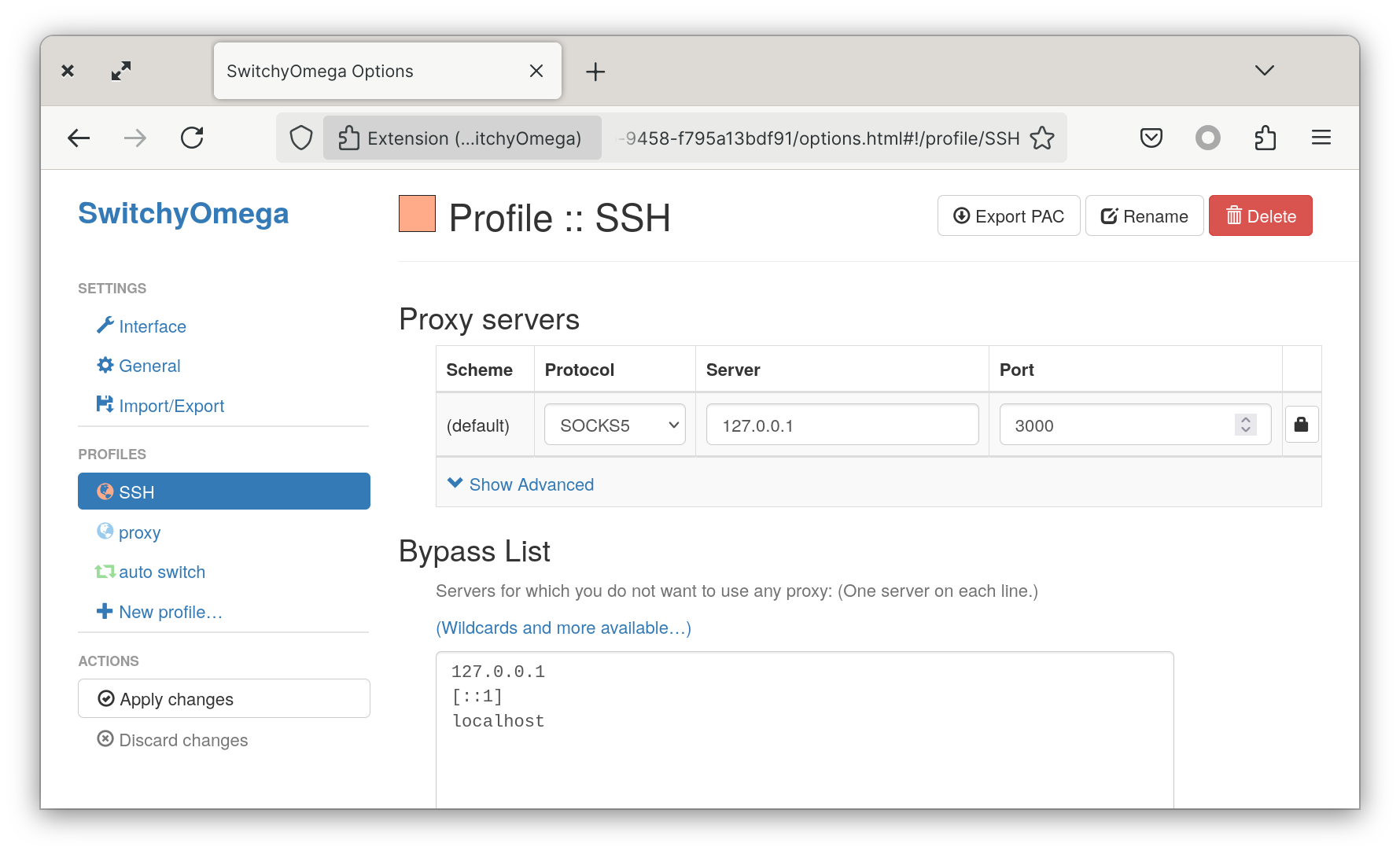
I create a new proxy in Switchy Omega as a Socks5 proxy defined as 127.0.0.1:3000.
You can select it in your list of proxies. And voilà, we have access to France TV.
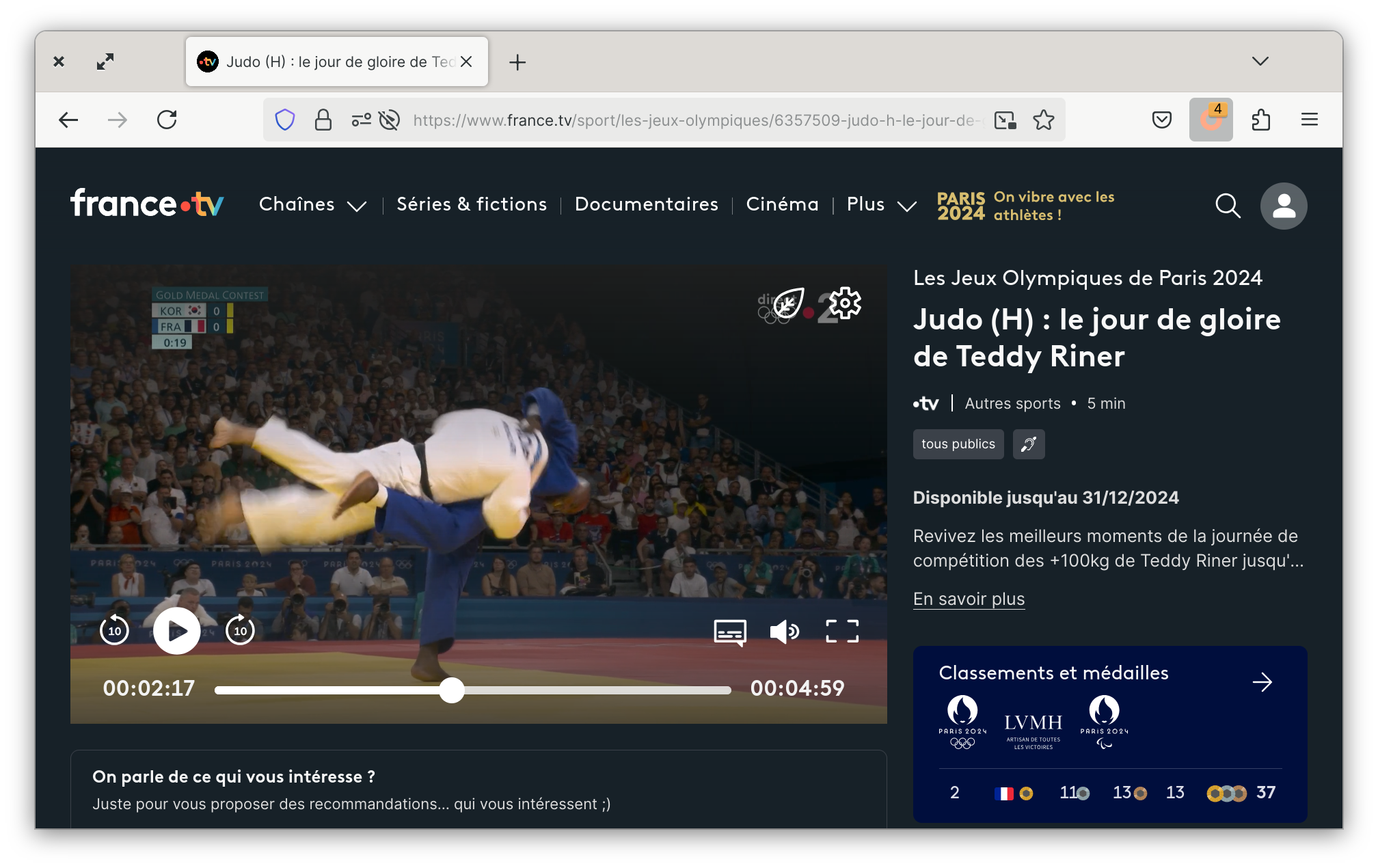
Awesome! What just happened?
Well, glad you ask. Let’s look at the ssh command. (On a side note, explainshell is really nice to explore shell commands.)
ssh -fND 127.0.0.1:3000 username@server
-findicates to runsshin background-Nindicates that we don’t want to run any commands (used for port forwarding).-Dis the interesting stuff. Let’s look at the man page.
-D [bind_address:]port: Specifies a local “dynamic” application-level port forwarding. This works by allocating a socket to listen to port on the local side, optionally bound to the specified bind_address.
Whenever a connection is made to this port, the connection is forwarded over the secure channel, and the application protocol is then used to determine where to connect to from the remote machine.
Currently the SOCKS4 and SOCKS5 protocols are supported, and ssh will act as a SOCKS server. Only root can forward privileged ports. Dynamic port forwardings can also be specified in the configuration file.
So -D let us create a SOCKS5 proxy, and the packets will be forwarded over SSH.
Nice, what’s a SOCKS5 proxy exactly?
A proxy is something that sits between you and the internet. It will relay your requests to the different websites.
For example, a company might deploy a proxy to block adult websites, shady websites, check for malware, log connections, etc.
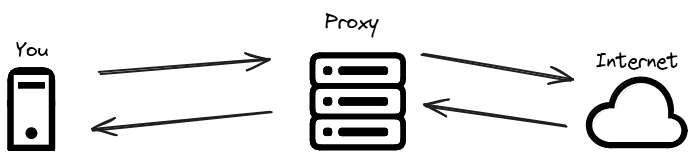
Traditional proxy are only for the HTTP protocol, but soon enough there was a need to offer the same service for other protocols.
SOCKS offer the same service at the TCP level. There are 2 major versions, SOCKS4 and SOCKS5. SOCKS5 is more modern and supports UDP, IPv6, and authentication.
SOCKS is a protocol, so the support for the protocol must be implemented. But luckily for us, it’s implemented in all major browsers. You can also proxify some apps that don’t implement SOCKS with tools like proxychains.